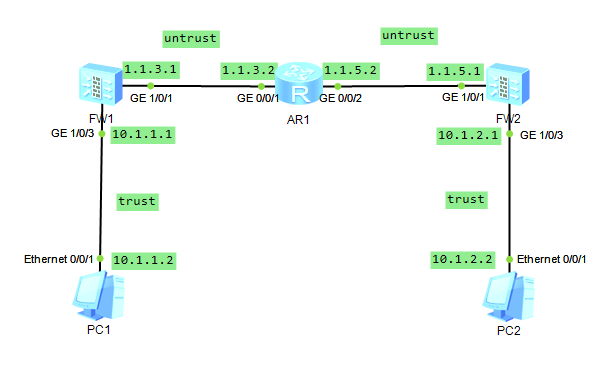
一、拓扑结构
防火墙型号:USG6000V
路由器型号:AR2220
拓扑文件及资料下载:
https://wwk.lanzouq.com/b0016fzpji
密码:szpu
二、配置过程
1、配置接口IP地址、区域、安全策略
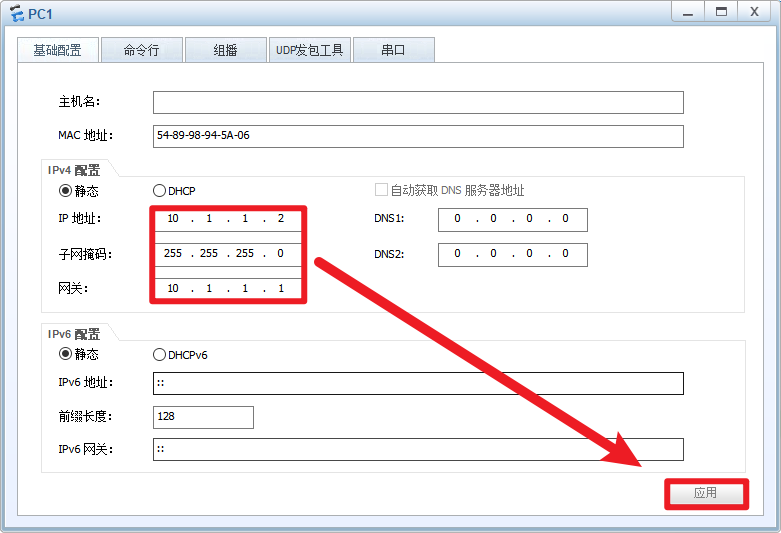
(1)配置PC1、PC2的IP地址、网关、掩码等
(2)在路由器接口上配置IP地址
AR1:
<Huawei>system-view
[Huawei]interface GigabitEthernet 0/0/1
[Huawei-GigabitEthernet0/0/1]ip address 1.1.3.2 24
[Huawei-GigabitEthernet0/0/1]quit
[Huawei]interface GigabitEthernet 0/0/2
[Huawei-GigabitEthernet0/0/2]ip address 1.1.5.2 24(3)FW1上的基础配置
初次登录,会要求修改密码
Username:admin
Password:Admin@123
统一要求:以后实操训练时,将密码统一修改为:Huawei@123
<USG6000V1>system-view
[USG6000V1]sysname FW1
[FW1]user-interface console 0
[FW1-ui-console0]idle-timeout 0
[FW1-ui-console0]quit
[FW1]undo info-center enable
[FW1]interface GigabitEthernet 1/0/1
[FW1-GigabitEthernet1/0/1]ip address 1.1.3.1 24
[FW1-GigabitEthernet1/0/1]quit
[FW1]interface GigabitEthernet 1/0/3
[FW1-GigabitEthernet1/0/3]ip address 10.1.1.1 24
[FW1-GigabitEthernet1/0/3]quit
[FW1]firewall zone trust
[FW1-zone-trust]add interface GigabitEthernet 1/0/3
[FW1-zone-trust]quit
[FW1]firewall zone untrust
[FW1-zone-untrust]add interface GigabitEthernet 1/0/1
[FW1-zone-untrust]quit
[FW1]security-policy
[FW1-policy-security]default action permit (回车后输入Y)
[FW1-policy-security]quit
[FW1]ip route-static 1.1.5.0 24 1.1.3.2(4)FW2上的基础配置
根据上一步修改FW2的密码,然后再进行以下的操作。
<USG6000V1>system-view
[USG6000V1]sysname FW2
[FW2]user-interface console 0
[FW2-ui-console0]idle-timeout 0
[FW2-ui-console0]quit
[FW2]undo info-center enable
[FW2]interface GigabitEthernet 1/0/1
[FW2-GigabitEthernet1/0/1]ip address 1.1.5.1 24
[FW2-GigabitEthernet1/0/1]quit
[FW2]interface GigabitEthernet 1/0/3
[FW2-GigabitEthernet1/0/3]ip address 10.1.2.1 24
[FW2-GigabitEthernet1/0/3]quit
[FW2]firewall zone trust
[FW2-zone-trust]add interface GigabitEthernet 1/0/3
[FW2-zone-trust]quit
[FW2]firewall zone untrust
[FW2-zone-untrust]add interface GigabitEthernet 1/0/1
[FW2-zone-untrust]quit
[FW2]security-policy
[FW2-policy-security]default action permit(回车后输入Y)
[FW2-policy-security]quit
[FW2]ip route-static 1.1.3.0 24 1.1.5.22、FW1上的IPSec相关配置
(1)通过配置高级ACL规则组来定义需要保护的数据流。
[FW1]acl 3000
[FW1-acl-adv-3000]rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
[FW1-acl-adv-3000]quit(2)配置IKE安全提议。
[FW1]ike proposal 10
[FW1-ike-proposal-10]quit(3)配置IPSec安全提议
[FW1]ipsec proposal tran1
[FW1-ipsec-proposal-tran1]quit(4)配置IKE peer
[FW1]ike peer b
[FW1-ike-peer-b] undo version 2
[FW1-ike-peer-b] ike-proposal 10
[FW1-ike-peer-b] remote-address 1.1.5.1
[FW1-ike-peer-b] pre-shared-key Test!1234
[FW1-ike-peer-b]quit(5)配置IPSec策略
[FW1]ipsec policy map1 10 isakmp
[FW1-ipsec-policy-isakmp-map1-10] security acl 3000
[FW1-ipsec-policy-isakmp-map1-10] proposal tran1
[FW1-ipsec-policy-isakmp-map1-10] ike-peer b
[FW1-ipsec-policy-isakmp-map1-10]quit(6)应用IPSec策略
[FW1]interface GigabitEthernet 1/0/1
[FW1-GigabitEthernet1/0/1]ipsec policy map1
[FW1-GigabitEthernet1/0/1]quit(7)配置引路路由
[FW1]ip route-static 10.1.2.0 24 GigabitEthernet 1/0/13、FW2上的IPSec相关配置
(1)通过配置高级ACL规则组来定义需要保护的数据流。
[FW2]acl 3000
[FW2-acl-adv-3000] rule 5 permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
[FW2-acl-adv-3000]quit(2)配置IKE安全提议。
[FW2]ike proposal 10
[FW2-ike-proposal-10]quit(3)配置IPSec安全提议
[FW2]ipsec proposal tran1
[FW2-ipsec-proposal-tran1]quit(4)配置IKE peer
[FW2]ike peer a
[FW2-ike-peer-a]undo version 2
[FW2-ike-peer-a]ike-proposal 10
[FW2-ike-peer-a]remote-address 1.1.3.1
[FW2-ike-peer-a]pre-shared-key Test!1234
[FW2-ike-peer-a]quit(5)配置IPSec策略
[FW2]ipsec policy map1 10 isakmp
[FW2-ipsec-policy-isakmp-map1-10]security acl 3000
[FW2-ipsec-policy-isakmp-map1-10]proposal tran1
[FW2-ipsec-policy-isakmp-map1-10]ike-peer a
[FW2-ipsec-policy-isakmp-map1-10]quit(6)应用IPSec策略
[FW2] interface GigabitEthernet 1/0/1
[FW2-GigabitEthernet1/0/1] ipsec policy map1
[FW2-GigabitEthernet1/0/1]quit(7)配置引路路由
[FW2] ip route-static 10.1.1.0 24 GigabitEthernet 1/0/1三、结果验证
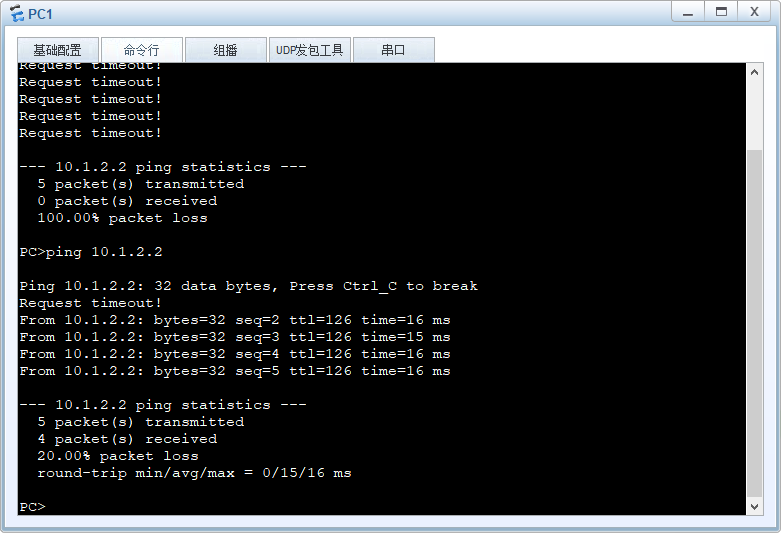
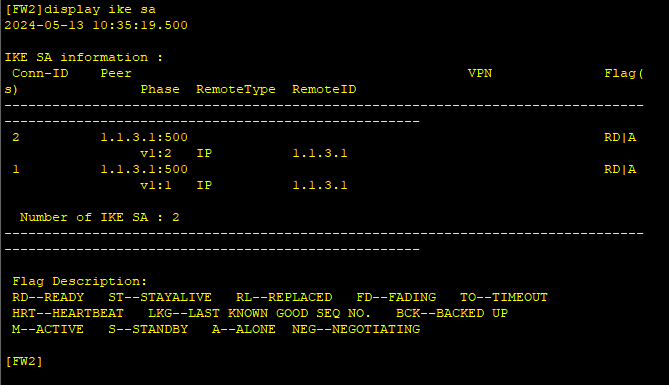
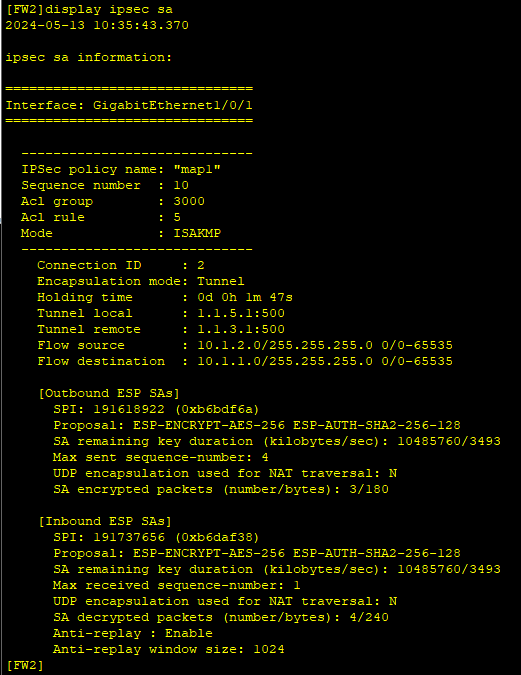
1、配置完成后,在PC1执行ping 10.1.2.2命令,触发IKE协商。
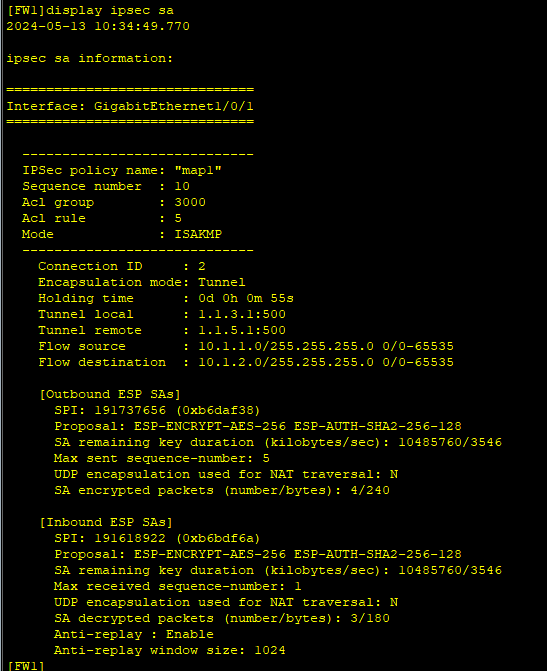
2、分别在FW1和FW2上执行display ike sa、display ipsec sa会显示安全联盟的建立情况。
FW1:
FW2:




近期评论