参考文章:https://blog.csdn.net/jjc321506301915/article/details/115362983
实验环境
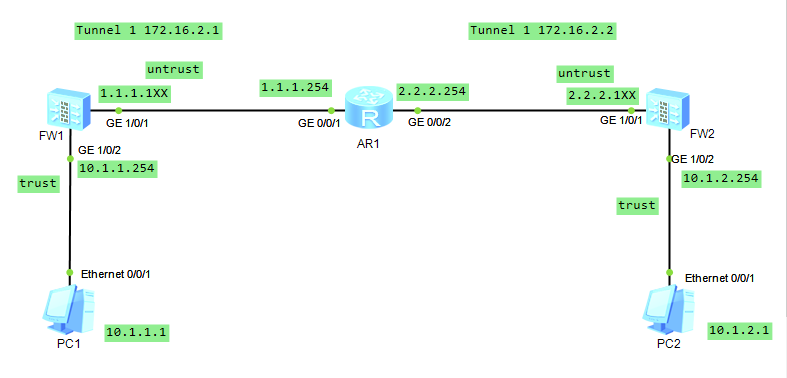
拓扑文件下载:
https://wwk.lanzouq.com/i2cXR1y1qzha
实验目的
需求描述:运行IP协议的两个子网网络1和网络2,通过在防火墙1和防火墙2之间建立的GRE隧道实现互访。要求防火墙上配置安全策略。
提交互访成功的截图,以及拓扑图。
实验思路
- 规划并配置IP
- 配置OSPF
- 划分区域
- 配置GRE
- 配置静态路由
- 配置安全策略
- 检查连通性
实验步骤
初始配置
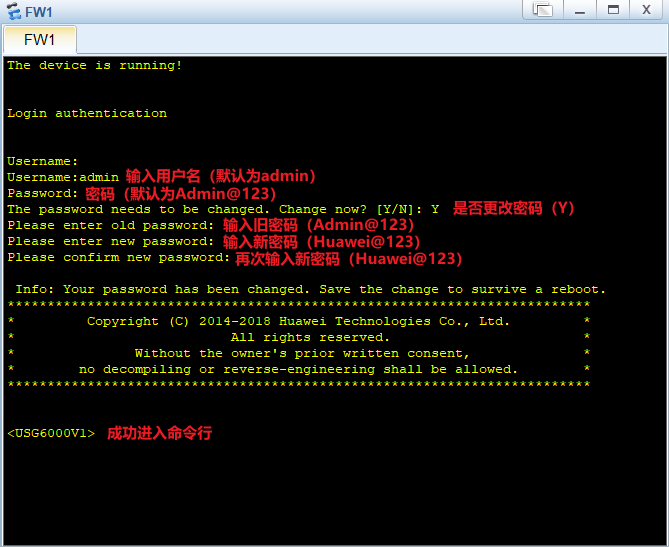
初次登录,会要求修改密码
Username:admin
Password:Admin@123
统一要求:以后实操训练时,将密码统一修改为:Huawei@123
FW1:
<USG6000V1>system-view
[USG6000V1]sysname FW1
[FW1]undo info-center enable
[FW1]user-interface console 0
[FW1-ui-console0]idle-timeout 0
[FW1-ui-console0]quitFW2:
<USG6000V1>system-view
[USG6000V1]sysname FW2
[FW2]undo info-center enable
[FW2]user-interface console 0
[FW2-ui-console0]idle-timeout 0
[FW2-ui-console0]quitAR1:
<Huawei>system-view
[Huawei]sysname AR
[AR]undo info-center enable
[AR]user-interface console 0
[AR-ui-console0]idle-timeout 0
[AR-ui-console0]quit规划并配置IP
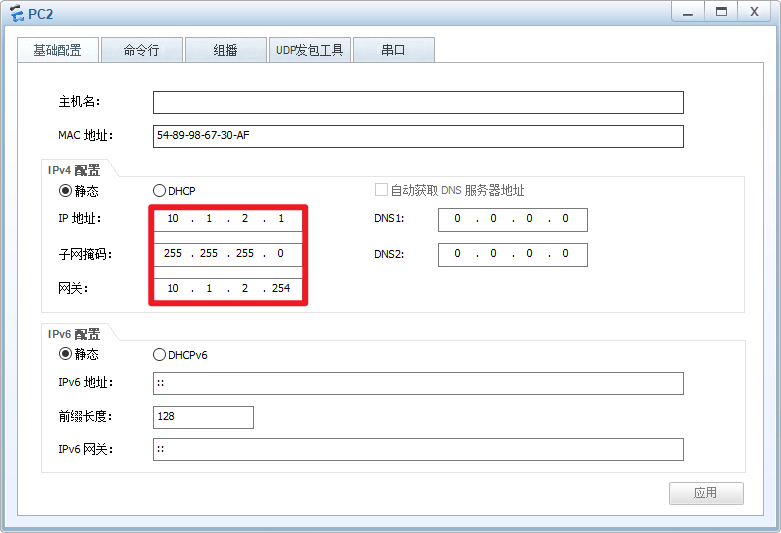
注意:配置完PC的IP地址后,记得点击右下角的“应用”!
PC1:
PC2:
FW1:
[FW1]int g1/0/1
# 此处xx为学号后两位
[FW1-GigabitEthernet1/0/1]ip add 1.1.1.1xx 24
[FW1-GigabitEthernet1/0/1]quit
[FW1]int g1/0/2
[FW1-GigabitEthernet1/0/2]ip add 10.1.1.254 24
[FW1-GigabitEthernet1/0/2]quit
[FW1]int Tunnel 1
[FW1-Tunnel1]ip add 172.16.2.1 24
[FW1-Tunnel1]quitFW2:
[FW2]int g1/0/1
# 此处xx为学号后两位
[FW2-GigabitEthernet1/0/1]ip add 2.2.2.1xx 24
[FW2-GigabitEthernet1/0/1]quit
[FW2]int g1/0/2
[FW2-GigabitEthernet1/0/2]ip add 10.1.2.254 24
[FW2-GigabitEthernet1/0/2]quit
[FW2]int Tunnel 1
[FW2-Tunnel1]ip add 172.16.2.2 24
[FW2-Tunnel1]quitAR1:
[AR]int g0/0/1
[AR-GigabitEthernet0/0/1]ip add 1.1.1.254 24
[AR-GigabitEthernet0/0/1]quit
[AR]int g0/0/2
[AR-GigabitEthernet0/0/2]ip add 2.2.2.254 24
[AR-GigabitEthernet0/0/2]quit配置OSPF
FW1:
[FW1]ospf
[FW1-ospf-1]area 0
# 此处xx为学号后两位
[FW1-ospf-1-area-0.0.0.0]network 1.1.1.1xx 0.0.0.0FW2:
[FW2]ospf
[FW2-ospf-1]area 0
# 此处xx为学号后两位
[FW2-ospf-1-area-0.0.0.0]network 2.2.2.1xx 0.0.0.0
AR1:
[AR]ospf
[AR-ospf-1]area 0
[AR-ospf-1-area-0.0.0.0]network 1.1.1.254 0.0.0.0
[AR-ospf-1-area-0.0.0.0]network 2.2.2.254 0.0.0.0划分区域
FW1:
[FW1]firewall zone trust
[FW1-zone-trust]add int g1/0/2
[FW1-zone-trust]firewall zone untrust
[FW1-zone-untrust]add int g1/0/1
[FW1]firewall zone dmz
[FW1-zone-dmz]add int Tunnel 1FW2:
[FW2]firewall zone trust
[FW2-zone-trust]add int g1/0/2
[FW2-zone-trust]firewall zone untrust
[FW2-zone-untrust]add int g1/0/1
[FW2-zone-untrust]firewall zone dmz
[FW2-zone-dmz]add int Tunnel 1配置GRE
FW1:
[FW1]int Tunnel 1
[FW1-Tunnel1]tunnel-protocol gre
# 此处xx为学号后两位
[FW1-Tunnel1]source 1.1.1.1xx
[FW1-Tunnel1]destination 2.2.2.1xxFW2:
[FW2]int Tunnel 1
[FW2-Tunnel1]tunnel-protocol gre
# 此处xx为学号后两位
[FW2-Tunnel1]source 2.2.2.1xx
[FW2-Tunnel1]destination 1.1.1.1xx配置静态路由
FW1:
[FW1]ip route-static 10.1.2.0 24 Tunnel 1FW2:
[FW2]ip route-static 10.1.1.0 24 Tunnel 1配置安全策略
FW1:
[FW1]security-policy
[FW1-policy-security]rule name u_l
[FW1-policy-security-rule-u_l]source-zone untrust
[FW1-policy-security-rule-u_l]destination-zone local
# 此处xx为学号后两位
[FW1-policy-security-rule-u_l]source-address 2.2.2.1xx 24
# 此处xx为学号后两位
[FW1-policy-security-rule-u_l]destination-address 1.1.1.1xx 24
[FW1-policy-security-rule-u_l]service gre
[FW1-policy-security-rule-u_l]action permit
[FW1-policy-security-rule-u_l]rule name t_d
[FW1-policy-security-rule-t_d]source-zone trust
[FW1-policy-security-rule-t_d]destination-zone dmz
[FW1-policy-security-rule-t_d]source-address 10.1.1.1 24
[FW1-policy-security-rule-t_d]destination-address 10.1.2.1 24
[FW1-policy-security-rule-t_d]service icmp
[FW1-policy-security-rule-t_d]action permitFW2:
[FW2]security-policy
[FW2-policy-security]rule name u_l
[FW2-policy-security-rule-u_l]source-zone untrust
[FW2-policy-security-rule-u_l]destination-zone local
# 此处xx为学号后两位
[FW2-policy-security-rule-u_l]source-address 1.1.1.1xx 24
[FW2-policy-security-rule-u_l]destination-address 2.2.2.1xx 24
[FW2-policy-security-rule-u_l]service gre
[FW2-policy-security-rule-u_l]action permit
[FW2-policy-security]rule name d_t
[FW2-policy-security-rule-d_t]source-zone dmz
[FW2-policy-security-rule-d_t]destination-zone trust
[FW2-policy-security-rule-d_t]source-address 10.1.1.1 24
[FW2-policy-security-rule-d_t]destination-address 10.1.2.1 24
[FW2-policy-security-rule-d_t]service icmp
[FW2-policy-security-rule-d_t]action permit检查连通性
PC1 ping PC2
对R3的g/0/2抓包
实验总结
通过本次实验学习了防火墙上的GRE配置。因为telnet流量属于防火墙自身收发,所以需要配置untrust区域到local区域的安全策略。GRE流量封装后,往外发送时是不需要匹配策略的,直接放行,但是接收时是需要匹配策略的。
实验注意:1.Tunnel要加入dmz区域。 2.配置策略:t_d ICMP 私网地址 ; u_l GRE 公网地址




近期评论