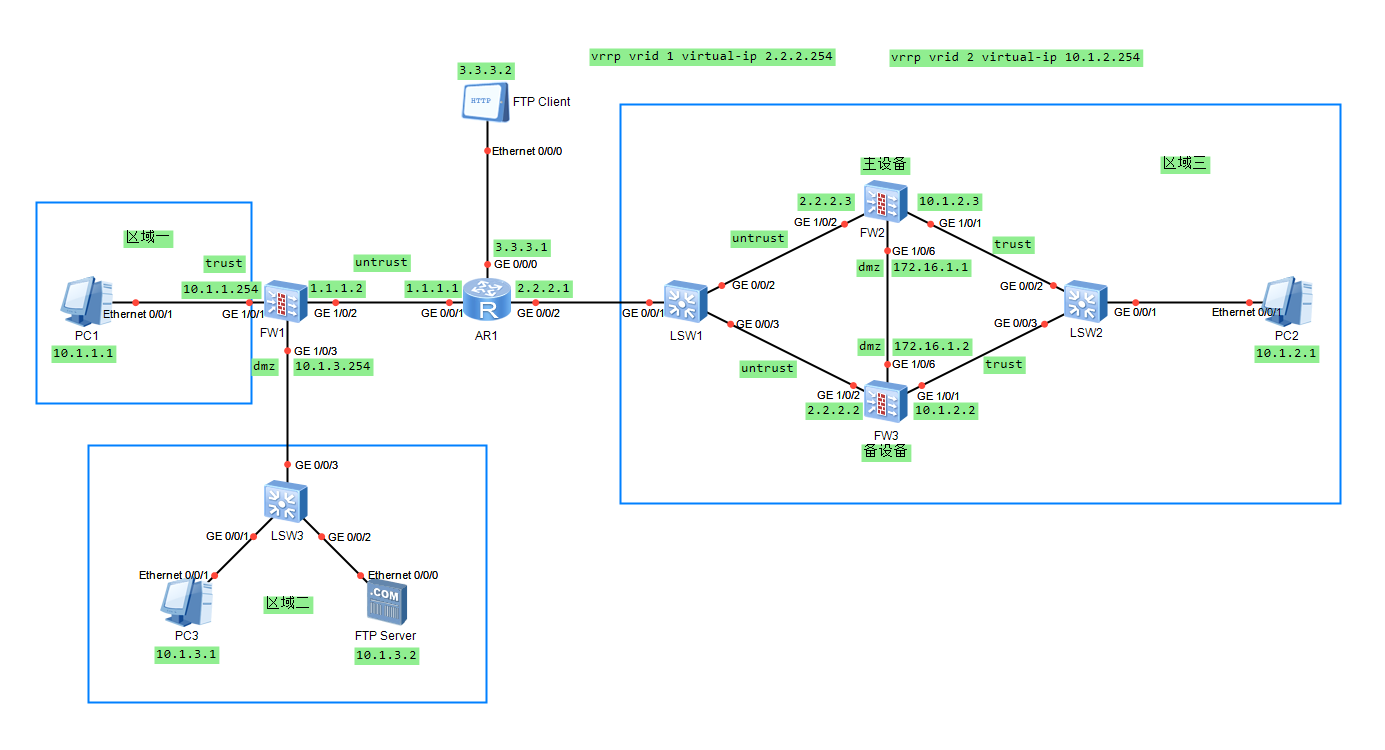
一、拓扑结构及要求
路由器:AR2220
交换机:S5700
防火墙:USG6000V
拓扑文件下载:
https://wwk.lanzouq.com/iixoh20dolvc
- 区域一访问外网(1.1.1.1)时,使用Easy IP
- 区域二访问外网(1.1.1.1)时,使用NAPT方式,地址池为8.8.8.8-8.8.8.8
- 外网的FTP Client可以通过公网地址9.9.9.9的100端口访问区域二的FTP服务器
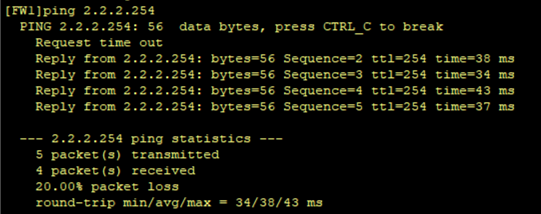
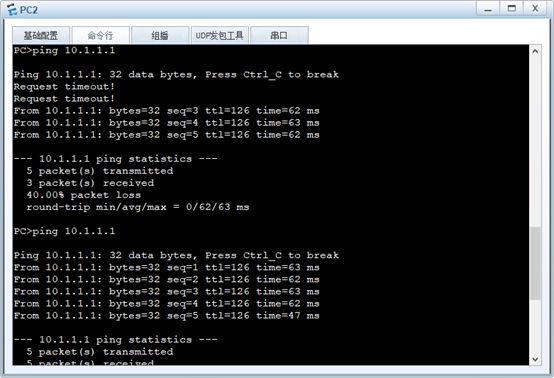
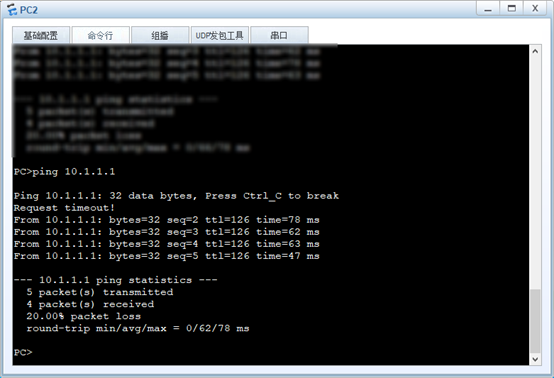
- FW2/FW3部署双机热备,采用主备备份方式,FW2为主设备,FW3为备设备,利用FW1去ping 2.2.2.254测试双机热备是否正常运行
- 区域三的计算机通过IPSec VPN(采用IKE方式)和区域一通信
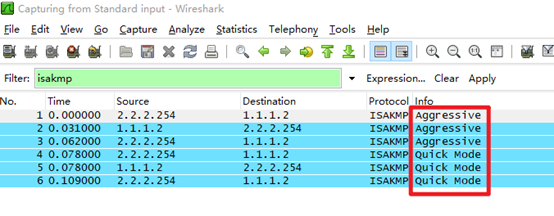
- 将交换模式由主模式更改为野蛮模式,在路由器左侧抓包查看报文交互情况,并截图
- 将安全协议由ESP更改为AH,在路由器左侧抓包查看报文交互情况,以及报文结构
二、配置过程
1、配置接口IP地址、区域、安全策略
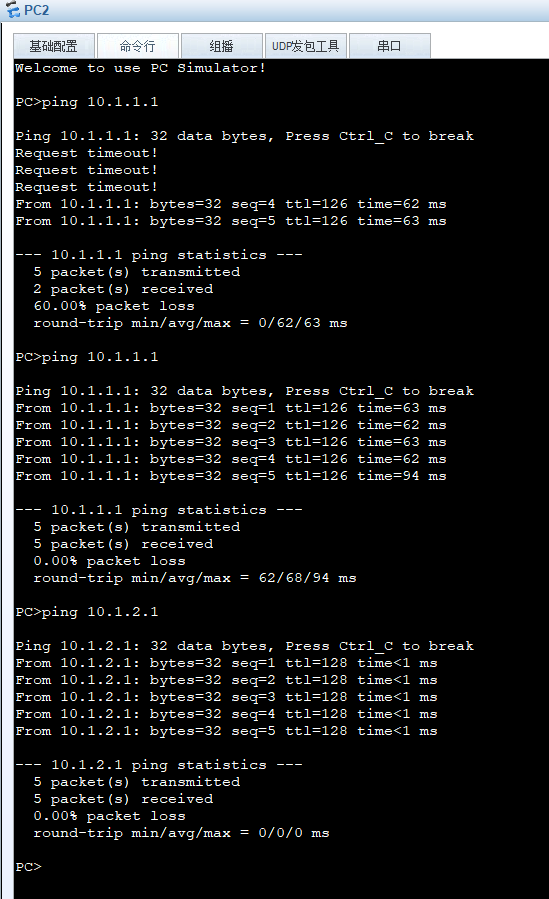
(1)配置PC1、PC2、PC3、FTP Client以及FTP Server的IP地址、网关、掩码等
| 主机名 | IP地址 | 子网掩码 | 默认网关 |
|---|---|---|---|
| PC1 | 10.1.1.1 | 255.255.255.0 | 10.1.1.254 |
| PC2 | 10.1.2.1 | 255.255.255.0 | 10.1.2.254 |
| PC3 | 10.1.3.1 | 255.255.255.0 | 10.1.3.254 |
| FTP Server | 10.1.3.2 | 255.255.255.0 | 10.1.3.254 |
| FTP Client | 3.3.3.2 | 255.255.255.0 | 3.3.3.1 |
(2)在路由器接口上配置IP地址
<Huawei>system-view
[Huawei]interface GigabitEthernet 0/0/0
[Huawei-GigabitEthernet0/0/0]ip address 3.3.3.1 24
[Huawei-GigabitEthernet0/0/0]quit
[Huawei]interface GigabitEthernet 0/0/1
[Huawei-GigabitEthernet0/0/1]ip address 1.1.1.1 24
[Huawei-GigabitEthernet0/0/1]quit
[Huawei]interface GigabitEthernet 0/0/2
[Huawei-GigabitEthernet0/0/2]ip address 2.2.2.1 24
[Huawei-GigabitEthernet0/0/2]quit(3)FW1上的基础配置
进入防火墙前请先修改初始密码,参考链接:https://www.19itmc.top/fw-tech/usg6000v-passwd.html
<USG6000V1>system-view
[USG6000V1]sysname FW1
[FW1]user-interface console 0
[FW1-ui-console0]idle-timeout 0
[FW1-ui-console0]quit
[FW1]interface GigabitEthernet 1/0/1
[FW1-GigabitEthernet1/0/1]ip address 10.1.1.254 24
[FW1-GigabitEthernet1/0/1]quit
[FW1]interface GigabitEthernet 1/0/2
[FW1-GigabitEthernet1/0/2]ip address 1.1.1.2 24
[FW1-GigabitEthernet1/0/2]quit
[FW1]interface GigabitEthernet 1/0/3
[FW1-GigabitEthernet1/0/3]ip address 10.1.3.254 24
[FW1-GigabitEthernet1/0/3]quit
[FW1]firewall zone trust
[FW1-zone-trust]add interface GigabitEthernet 1/0/1
[FW1-zone-trust]quit
[FW1]firewall zone untrust
[FW1-zone-untrust]add interface GigabitEthernet 1/0/2
[FW1-zone-untrust]quit
[FW1]firewall zone dmz
[FW1-zone-dmz]add interface GigabitEthernet 1/0/3
[FW1-zone-dmz]quit
[FW1]security-policy
[FW1-policy-security]default action permit (回车后输入Y)
[FW1]ip route-static 0.0.0.0 0 1.1.1.1(4)FW2上的基础配置
进入防火墙前请先修改初始密码,参考链接:https://www.19itmc.top/fw-tech/usg6000v-passwd.html
<USG6000V1>system-view
[USG6000V1]sysname FW2
[FW2]user-interface console 0
[FW2-ui-console0]idle-timeout 0
[FW2-ui-console0]quit
[FW2]interface GigabitEthernet 1/0/1
[FW2-GigabitEthernet1/0/1]ip address 10.1.2.3 24
[FW2-GigabitEthernet1/0/1]quit
[FW2]interface GigabitEthernet 1/0/2
[FW2-GigabitEthernet1/0/2]ip address 2.2.2.3 24
[FW2-GigabitEthernet1/0/2]quit
FW2]interface GigabitEthernet 1/0/6
[FW2-GigabitEthernet1/0/6]ip address 172.16.1.1 24
[FW2-GigabitEthernet1/0/6]quit
[FW2]firewall zone trust
[FW2-zone-trust]add interface GigabitEthernet 1/0/1
[FW2-zone-trust]quit
[FW2]firewall zone untrust
[FW2-zone-untrust]add interface GigabitEthernet 1/0/2
[FW2-zone-untrust]quit
[FW2]firewall zone dmz
[FW2-zone-dmz]add interface GigabitEthernet 1/0/6
[FW2-zone-dmz]quit
[FW2]security-policy
[FW2-policy-security]default action permit(回车后输入Y)
[FW2-policy-security]quit
[FW2]ip route-static 0.0.0.0 0 2.2.2.1(5)FW3上的基础配置
进入防火墙前请先修改初始密码,参考链接:https://www.19itmc.top/fw-tech/usg6000v-passwd.html
<USG6000V1>system-view
[USG6000V1]sysname FW3
[FW3]user-interface console 0
[FW3-ui-console0]idle-timeout 0
[FW3-ui-console0]quit
[FW3]interface GigabitEthernet 1/0/1
[FW3-GigabitEthernet1/0/1]ip address 10.1.2.2 24
[FW3-GigabitEthernet1/0/1]quit
[FW3]interface GigabitEthernet 1/0/2
[FW3-GigabitEthernet1/0/2]ip address 2.2.2.2 24
[FW3-GigabitEthernet1/0/2]quit
[FW3]interface GigabitEthernet 1/0/6
[FW3-GigabitEthernet1/0/6]ip address 172.16.1.2 24
[FW3-GigabitEthernet1/0/6]quit
[FW3]firewall zone trust
[FW3-zone-trust]add interface GigabitEthernet 1/0/1
[FW3-zone-trust]quit
[FW3]firewall zone untrust
[FW3-zone-untrust]add interface GigabitEthernet 1/0/2
[FW3-zone-untrust]quit
[FW3]firewall zone dmz
[FW3-zone-dmz]add interface GigabitEthernet 1/0/6
[FW3-zone-dmz]quit
[FW3]security-policy
[FW3-policy-security]default action permit(回车后输入Y)
[FW3-policy-security]quit
[FW3] ip route-static 0.0.0.0 0 2.2.2.11.区域一访问外网(1.1.1.1)时,使用Easy IP
[FW1]nat-policy
[FW1-policy-nat]rule name easyip
[FW1-policy-nat-rule-easyip]source-zone trust
[FW1-policy-nat-rule-easyip]destination-zone untrust
[FW1-policy-nat-rule-easyip]source-address 10.1.1.0 24
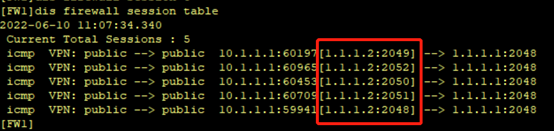
[FW1-policy-nat-rule-easyip]action source-nat easy-ip执行下图命令,如果没有结果重新PING一次,再进行查看。1.1.1.2:xxxx后面的端口号每次都不一样。
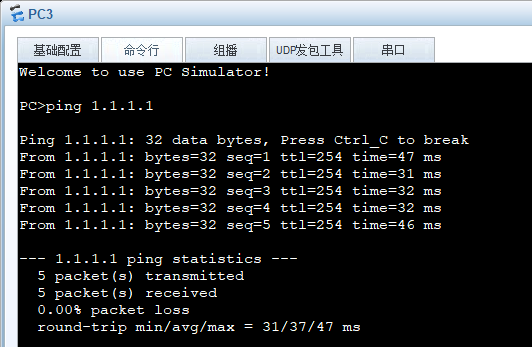
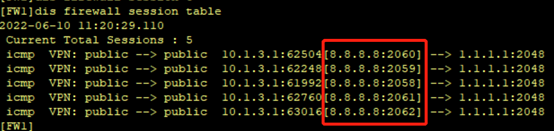
2.区域二访问外网(1.1.1.1)时,使用NAPT方式,地址池为8.8.8.8-8.8.8.8
[FW1]nat address-group 1
[FW1-address-group-1]section 8.8.8.8 8.8.8.8
[FW1-address-group-1]mode pat
[FW1-address-group-1]route enable
[FW1-address-group-1]quit
[FW1]nat-policy
[FW1-policy-nat] rule name napt
[FW1-policy-nat-rule-napt] source-zone dmz
[FW1-policy-nat-rule-napt] destination-zone untrust
[FW1-policy-nat-rule-napt] source-address 10.1.3.0 mask 255.255.255.0
[FW1-policy-nat-rule-napt] action source-nat address-group 1[Huawei]ip route-static 8.8.8.8 32 1.1.1.2执行下图命令,如果没有结果重新PING一次,再进行查看。8.8.8.8:xxxx后面的端口号每次都不一样。
3.外网的FTP Client可以通过公网地址9.9.9.9的100端口访问区域二的FTP服务器
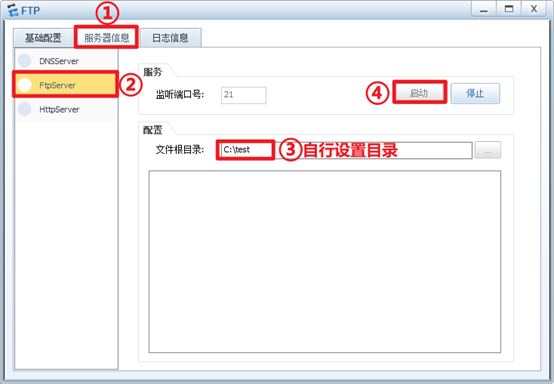
[Huawei]ip route-static 9.9.9.9 32 1.1.1.2[FW1]nat server ser1 protocol tcp global 9.9.9.9 100 inside 10.1.3.2 21 no-reverse unr-routeFTP Server上启动FTP服务,可自行设置目录,建议在设置的目录下新建一个文件,以便分辨是否登录成功。
在FTP Client上登录。
4.FW2/FW3部署双机热备,采用主备备份方式,FW2为主设备,FW3为备设备,利用FW1去ping 2.2.2.254测试双机热备是否正常运行
FW2上的双机热备相关配置
(1)配置VRRP备份组
[FW2]interface GigabitEthernet 1/0/1
[FW2-GigabitEthernet1/0/1]vrrp vrid 2 virtual-ip 10.1.2.254 active
[FW2-GigabitEthernet1/0/1]quit
[FW2]interface GigabitEthernet 1/0/2
[FW2-GigabitEthernet1/0/2]vrrp vrid 1 virtual-ip 2.2.2.254 active
[FW2-GigabitEthernet1/0/2]quit(2)指定心跳口并启用双机热备功能
[FW2]hrp interface GigabitEthernet 1/0/6 remote 172.16.1.2
[FW2]hrp enableFW3上的双机热备相关配置
(1)配置VRRP备份组
[FW3]interface GigabitEthernet 1/0/1
[FW3-GigabitEthernet1/0/1]vrrp vrid 2 virtual-ip 10.1.2.254 standby
[FW3-GigabitEthernet1/0/1]quit
[FW3]interface GigabitEthernet 1/0/2
[FW3-GigabitEthernet1/0/2]vrrp vrid 1 virtual-ip 2.2.2.254 standby
[FW3-GigabitEthernet1/0/2]quit(2)指定心跳口并启用双机热备功能
[FW3]hrp interface GigabitEthernet 1/0/6 remote 172.16.1.1
[FW3]hrp enableHRP_M[FW2]interface GigabitEthernet 1/0/2
HRP_M[FW2-GigabitEthernet1/0/2]service-manage ping permitHRP_S[FW3]hrp standby config enable
HRP_S[FW3]interface GigabitEthernet 1/0/2
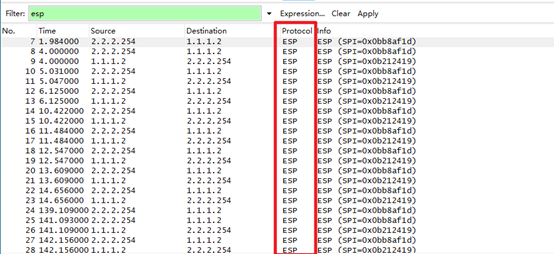
HRP_S[FW3-GigabitEthernet1/0/2]service-manage ping permit5.区域三的计算机通过IPSec VPN(采用IKE方式)和区域一通信,在路由器AR1左侧抓包查看报文加密情况,把结果截屏上交
FW1上的IPSec相关配置
(1)通过配置高级ACL规则组来定义需要保护的数据流。
[FW1] acl 3000
[FW1-acl-adv-3000] rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255(2)配置IKE安全提议。
[FW1] ike proposal 10(3)配置IPSec安全提议
[FW1] ipsec proposal tran1(4)配置IKE peer
[FW1] ike peer fzjg
[FW1-ike-peer- fzjg] undo version 2
[FW1-ike-peer- fzjg] ike-proposal 10
[FW1-ike-peer- fzjg] pre-shared-key Test!1234
[FW1-ike-peer- fzjg] remote-address 2.2.2.254(5)配置IPSec策略
[FW1] ipsec policy map1 1 isakmp
[FW1-ipsec-policy-isakmp-map1-1] security acl 3000
[FW1-ipsec-policy-isakmp-map1-1] proposal tran1
[FW1-ipsec-policy-isakmp-map1-1] ike-peer fzjg(6)应用IPSec策略
[FW1] interface GigabitEthernet 1/0/2
[FW1-GigabitEthernet1/0/2] ipsec policy map1(7)配置引路路由
[FW1] ip route-static 10.1.2.0 24 1.1.1.1(8)配置no-pat策略
[FW1]nat-policy
[FW1-policy-nat]rule name ipsec
[FW1-policy-nat-rule-ipsec]source-address 10.1.1.0 24
[FW1-policy-nat-rule-ipsec]destination-address 10.1.2.0 24
[FW1-policy-nat-rule-ipsec]action no-nat
[FW1-policy-nat-rule-ipsec]quit
[FW1-policy-nat]rule move ipsec topFW2上的IPSec相关配置
(1)通过配置高级ACL规则组来定义需要保护的数据流。
#回车后会出现(+B)
HRP_M[FW2]acl 3000
HRP_M[FW2-acl-adv-3000] rule 5 permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255(2)配置IKE安全提议。
HRP_M[FW2] ike proposal 10(3)配置IPSec安全提议
HRP_M[FW2] ipsec proposal tran1(4)配置IKE peer
HRP_M[FW2-ike-peer-zb] ike peer zb
HRP_M[FW2-ike-peer-zb]undo version 2
HRP_M[FW2-ike-peer-zb] ike-proposal 10
HRP_M[FW2-ike-peer-zb] remote-address 1.1.1.2
HRP_M[FW2-ike-peer-zb] pre-shared-key Test!1234(5)配置IPSec策略
HRP_M[FW2] ipsec policy map1 10 isakmp
HRP_M[FW2-ipsec-policy-isakmp-map1-10] security acl 3000
HRP_M[FW2-ipsec-policy-isakmp-map1-10] proposal tran1
HRP_M[FW2-ipsec-policy-isakmp-map1-10] ike-peer zb
HRP_M[FW2-ipsec-policy-isakmp-map1-10]tunnel local 2.2.2.254(6)应用IPSec策略
HRP_M[FW2]interface GigabitEthernet 1/0/2
HRP_M[FW2-GigabitEthernet1/0/2] ipsec policy map1(7)配置引路路由
#注意此条命令回车后没有出现(+B)
HRP_M[FW2] ip route-static 10.1.1.0 24 2.2.2.1FW3上的IPSec相关配置
(1)配置引路路由
HRP_S[FW3] ip route-static 10.1.1.0 24 2.2.2.1在路由器G0/0/1接口进行抓包:
6.将交换模式由主模式更改为野蛮模式,在路由器左侧抓包查看报文交互情况,并截图
[FW1]ike peer fzjg
[FW1-ike-peer-fzjg]exchange-mode aggressiveHRP_M[FW2]ike peer zb
HRP_M[FW2-ike-peer-zb]exchange-mode aggressiveHRP_M<FW2>reset ike sa (回车后输入Y)HRP_S<FW3>reset ike sa (回车后输入Y)<FW1>reset ike sa(回车后输入Y)在路由器G0/0/1接口进行抓包:
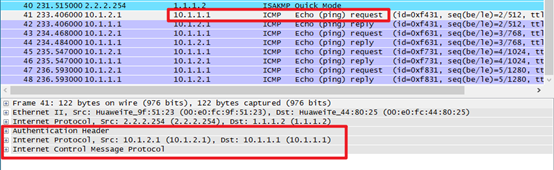
7.将安全协议由ESP更改为AH,在路由器左侧抓包查看报文交互情况,以及报文结构
[FW1]ipsec proposal tran1
[FW1-ipsec-proposal-tran1]transform ahHRP_M[FW2]ipsec proposal tran1
HRP_M[FW2-ipsec-proposal-tran1]transform ahHRP_M<FW2>reset ike sa (回车后输入Y)HRP_S<FW3>reset ike sa (回车后输入Y)<FW1>reset ike sa(回车后输入Y)三、保存拓扑文件
回车后输入Y。
<FW1>save
HRP_M<FW2>save
HRP_S<FW3>save
<Huawei>save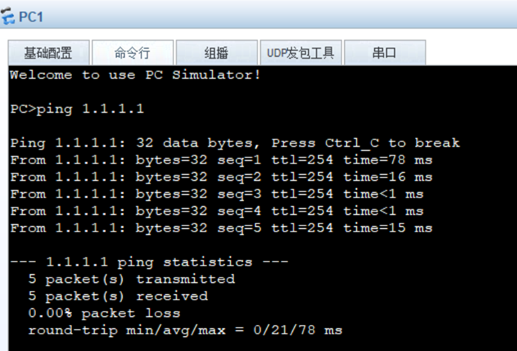


近期评论