网络拓扑
拓扑文件下载:
https://wwk.lanzouq.com/ijtMc1y1o6tg
题目
配置防火墙的NAT策略(PAT模式),使得内网(左边)可以访问外网,使用地址池:2.2.2.1XX。要求在配置中加入黑洞路由、安全策略。测试从内网访问外网ping 192.168.1.1,使用disp firewall session table,把测试结果截屏,连同拓扑图一起提交。
配置
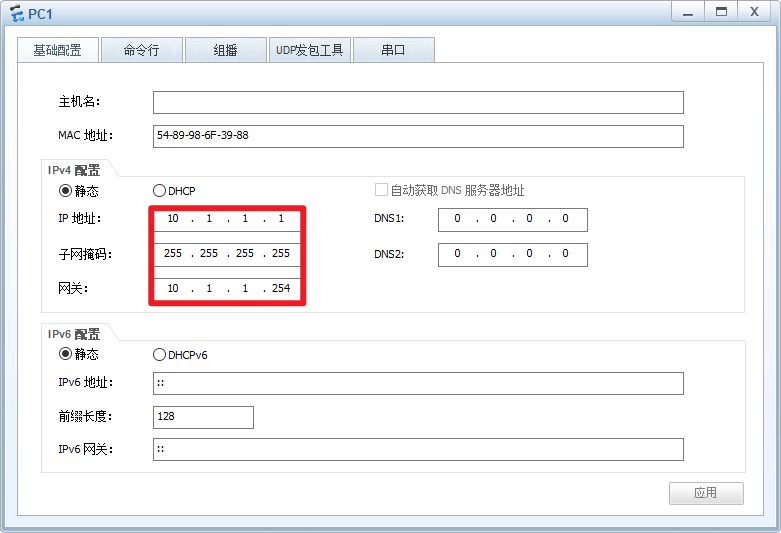
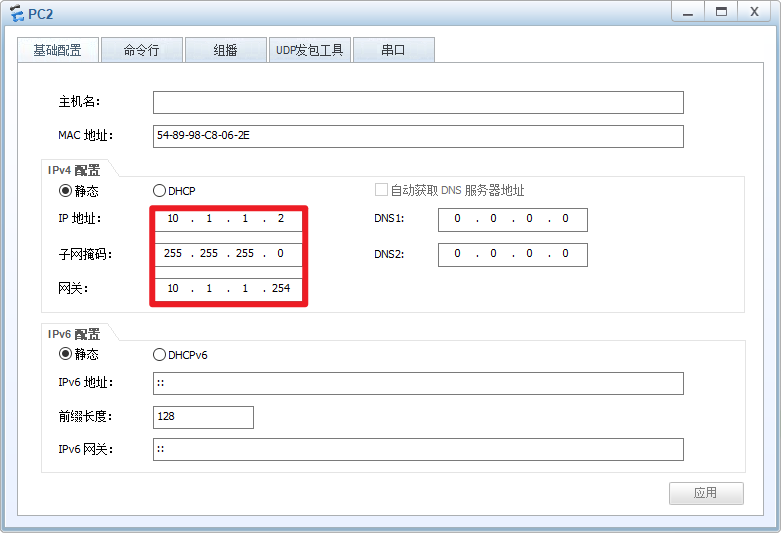
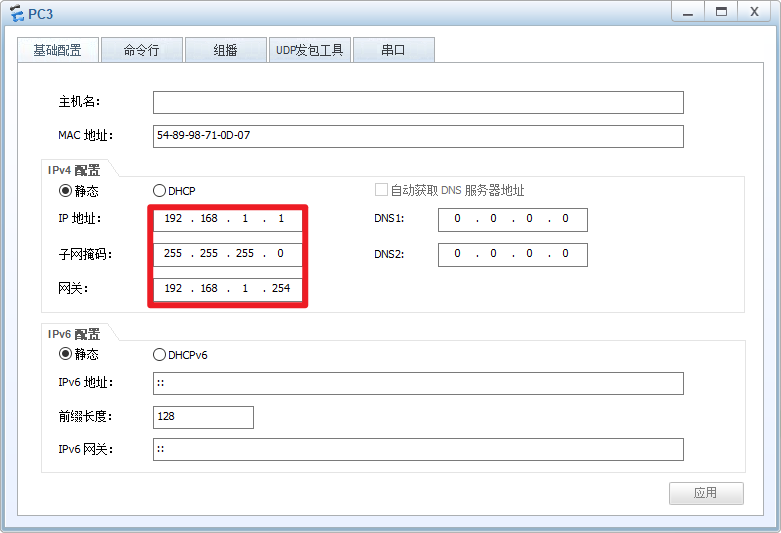
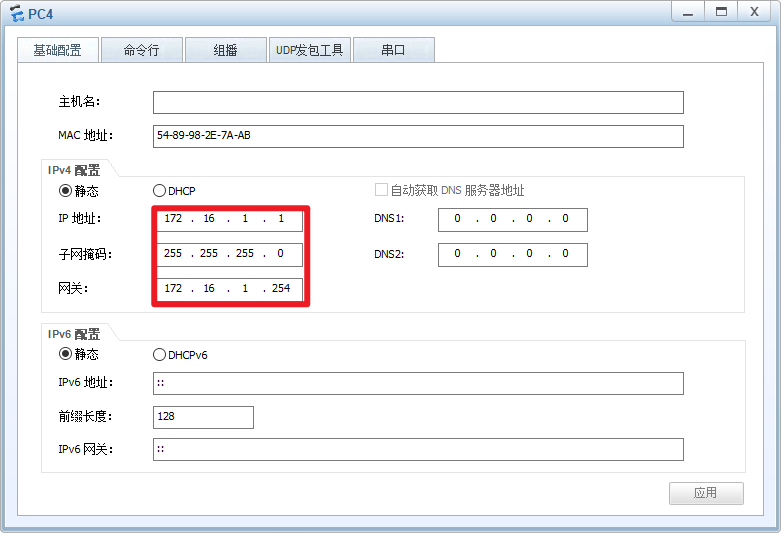
注意:配置完PC的IP地址后,记得点击右下角的“应用”!
PC1:
PC2:
PC3:
PC4:
AR1:
<Huawei>system-view
[Huawei]sysname AR1
[AR1]int g0/0/0
[AR1-GigabitEthernet0/0/0]ip address 1.1.1.1 24
[AR1-GigabitEthernet0/0/0]quit
[AR1]int g0/0/1
[AR1-GigabitEthernet0/0/1]ip add 192.168.1.254 24
[AR1-GigabitEthernet0/0/1]quit
[AR1]ip route-static 2.2.2.0 24 1.1.1.254AR2:
<Huawei>system-view
[Huawei]sysname AR2
[AR2]int g0/0/1
[AR2-GigabitEthernet0/0/1]ip address 3.3.3.1 24
[AR2-GigabitEthernet0/0/1]quit
[AR2]int g0/0/2
[AR2-GigabitEthernet0/0/2]ip address 172.16.1.254 24
[AR2-GigabitEthernet0/0/2]quit
[AR2]ip route-static 2.2.2.0 24 3.3.3.254FW1:
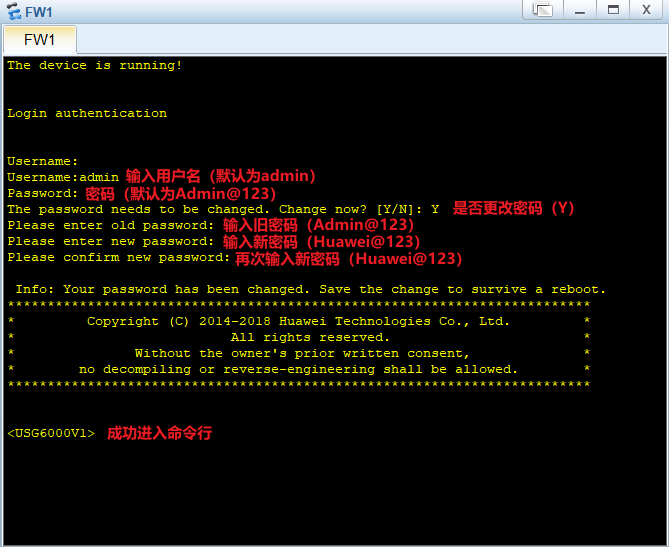
初次登录,会要求修改密码
Username:admin
Password:Admin@123
统一要求:以后实操训练时,将密码统一修改为:Huawei@123
<USG6000V1>system-view
# 设置设备名称为FW,此处FW可更改为姓名拼音
[USG6000V1]sysname FW
[FW]undo info-center enable
[FW]user-interface console 0
[FW-ui-console0]idle-timeout 0
[FW-ui-console0]quit
[FW]int g1/0/1
[FW-GigabitEthernet1/0/1]ip address 10.1.1.254 24
[FW-GigabitEthernet1/0/1]quit
[FW]int g1/0/2
[FW-GigabitEthernet1/0/2]ip address 1.1.1.254 24
[FW-GigabitEthernet1/0/2]quit
[FW]int g1/0/3
[FW-GigabitEthernet1/0/3]ip address 3.3.3.254 24
[FW-GigabitEthernet1/0/3]quit
[FW]firewall zone trust
[FW-zone-trust]add int g1/0/1
[FW-zone-trust]quit
[FW]firewall zone untrust
[FW-zone-untrust]add int g1/0/2
[FW-zone-untrust]quit
[FW]firewall zone dmz
[FW-zone-dmz]add int g1/0/3
[FW-zone-dmz]quit
[FW]ip route-static 0.0.0.0 0 1.1.1.1
[FW]nat address-group 1 0
[FW-address-group-1]mode no-pat local
[FW-address-group-1]section 0 2.2.2.1 2.2.2.1
[FW-address-group-1]quit
# 此处2.2.2.102中的102可更改为1xx,(xx为学号后两位)
[FW]nat address-group 2.2.2.102 1
[FW-address-group-2.2.2.102]mode no-pat global
[FW-address-group-2.2.2.102]route enable
# 此处2.2.2.102中的102可更改为1xx,(xx为学号后两位)
[FW-address-group-2.2.2.102]section 0 2.2.2.102 2.2.2.102
[FW-address-group-2.2.2.102]quit
[FW]security-policy
[FW-policy-security]rule name 1
[FW-policy-security-rule-1]source-zone trust
[FW-policy-security-rule-1]destination-zone dmz
[FW-policy-security-rule-1]destination-zone untrust
[FW-policy-security-rule-1]source-address 10.1.1.0 24
[FW-policy-security-rule-1]action permit
[FW-policy-security-rule-1]quit
[FW-policy-security]quit
[FW]nat-policy
[FW-policy-nat]rule name 1
[FW-policy-nat-rule-1]source-zone trust
[FW-policy-nat-rule-1]destination-zone dmz
[FW-policy-nat-rule-1]destination-zone untrust
[FW-policy-nat-rule-1]source-address 10.1.1.0 24
# 此处2.2.2.102中的102可更改为1xx,(xx为学号后两位)
[FW-policy-nat-rule-1]action source-nat address-group 2.2.2.102
[FW-policy-nat-rule-1]quit
[FW-policy-nat]rule name naet1
[FW-policy-nat-rule-naet1]source-zone untrust
[FW-policy-nat-rule-naet1]destination-zone dmz
[FW-policy-nat-rule-naet1]destination-zone trust
[FW-policy-nat-rule-naet1]source-address 10.1.1.0 24
# 此处2.2.2.102中的102可更改为1xx,(xx为学号后两位)
[FW-policy-nat-rule-naet1]action source-nat address-group 2.2.2.102
[FW-policy-nat-rule-naet1]quit
[FW-policy-nat]quit
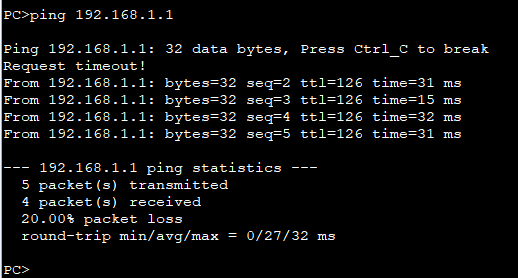
[FW]在PC1的命令行ping 192.168.1.1:
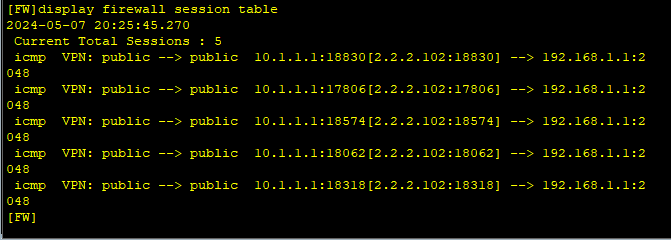
在FW1使用display firewall session table命令查看:
注意:下图的2.2.2.102中的102为学号,格式为1xx(xx为学号)
保存拓扑文件
<FW>save # 回车后输入Y
<AR>save # 回车后输入Y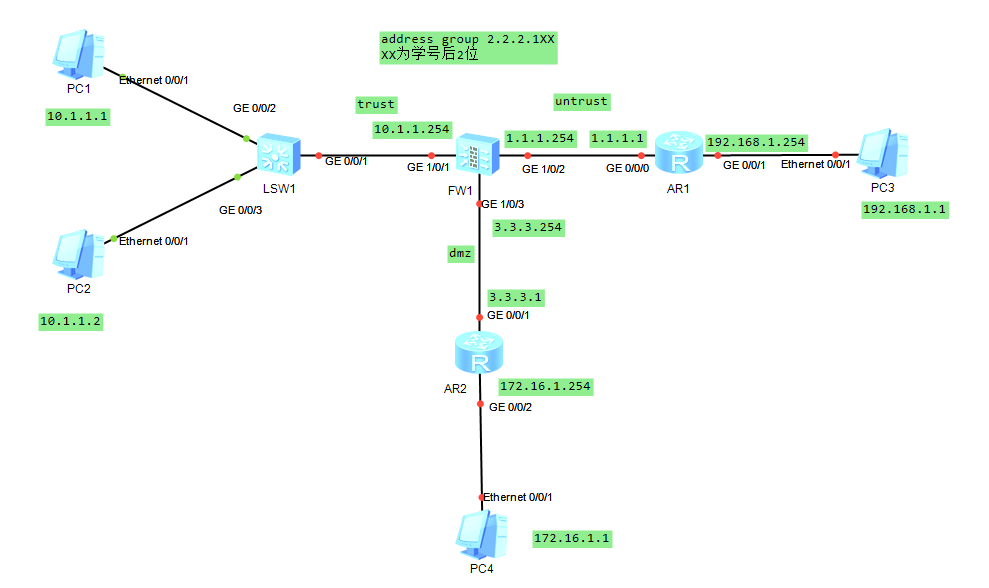

近期评论